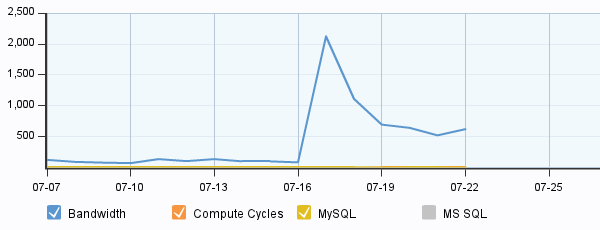
With pacman development progressing smoothly towards an upcoming 4.0.0 release, I thought it would be nice to write about everybody’s favourite (and a not at all controversial) topic… package signing. I will separate the discussion into several parts over the coming weeks, writing about a new area when I personally consider the interface in that area to being relatively finalised. That is not to say what is written about here will not change before the final release, just that I find it unlikely. Note also that I will focusing more on the technical details of the package signing implementation in pacman and its tools. So there will be limited discussion on issues a distribution may face using these features and I will not be specifically covering how Arch Linux will make use of these features.
The first thing that you are going to need to sign packages and repo databases is a PGP key. All the details of creating one using GnuPG can be found elsewhere. The only real consideration is the choice of key type. Currently a 2048-bit RSA key seems to be the gold standard. Going to 4096-bit is probably excessive and being a larger key has the side effect of slowing down the verification process (to an extent that is noticeable on older CPUs).
Once you have that sorted, it is time to sign some packages using makepkg. The implementation is quite simple. When a package signature is needed, makepkg simply calls gpg --detach-sign on the package(s) it creates. If you have the GnuPG-Agent is running, you will not even be asked for your passphrase (depending on your set-up). Deciding whether to sign packages or not is primarily controlled through the “sign” BUILDENV option in makepkg.conf, but can be overridden on the command line using --sign or --nosign. By default, the package will be signed with your primary PGP key. If you wish to use another key, you can set the GPGKEY variable (either in makepkg.conf or the environment), or use the --key option with makepkg.
The additions to repo-add are similarly simple. When adding a package to a repo database, repo-add checks for a detached signature and if present adds it to the package description entry, ready for libalpm to process. Finally, signing packages is not enough. We also need the ability to sign the package database (e.g. to prevent the holding back of an update to an individual package containing a security vulnerability). This is done using similar options to makepkg, with -s/--sign to tell repo-add to sign the database and --key (or the environmental variable GPGKEY) to select a non-default GPG key to sign with. In addition, repo-add has a -v/--verify flag that checks the current signature is valid before proceeding (very important as repo-add adjusts the current database rather than regenerating it from scratch).
As an aside, a couple of other useful security features have made their way into makepkg and repo-add during this development cycle. The ability to automatically check PGP signatures for source files has been added to makepkg (thanks to first time contributer Wieland Hoffmann). This is done by detecting files in the source ending in the standard extensions .sig and .asc. A source file and signature can be quickly be specified using bash expansion like:
sources=($pkgname-$pkgver.tar.gz{,.sig})
which makes it quite clear which source files have signatures. If wanted, this check can be skipped using the --skippgpcheck or the --skipinteg options (the latter of which also ships checksum checks). Also, repo-add includes a SHA256 checksum in the repo database in addition the the current MD5 checksum, although currently libalpm (and thus pacman) does nothing with this entry. (Despite some prior assertion, adding that properly took more than a one line change… but I will leave that there.)
Finally, a quick note on the challenges faced by distributions using these tools for package and database signing. The facilities provided by makepkg and repo-add work well for repositories where the packages get built locally, added to the repo database and then mirrored to their server (such as the repo I provide), but may not be ideal to use for a larger distribution repository maintained by multiple people. For example, if building a package on an remote build server, then the packager should not want to put their private PGP key onto that server to sign the package. It currently appears that there is no easy way around this, so the package building and signing steps need to be separated, with the built package downloaded locally and then signed (although this may change in future GnuPG releases as I see patches have been recently submitted to their mailing list providing a proof-of-concept implementation to improve remote signing functionality). Similarly, how is it best to sign a repository database that is added to by multiple packagers? Having some sort of master key sign it requires some sort of reduction in security of the passphrase (with either all people pushing to the repo knowing it or having it somehow accessible to the script adding the packages to the repo database). If set-up with care, this may be acceptably low risk for a distribution to use (and, from what I understand, this is what is done by several distributions), but personally I do not see it as an ideal solution. And that brings us back to the issue of how to best sign a remote file. So, implementing the tools may actually be the simple part in all of this…
 So I decided to create a very simple theme based on the archlinux-simplyblack theme provided in the archlinux-themes-slim package. I dislike all the options crap typically displayed in a login manager, so this theme will not show a user selection dialog, session manager, keyboard layout changer, language selection or even a quit dialog, no matter what your configuration is. Also my guess is that this theme only works with the GTK greeter given I have not tested anything else…
So I decided to create a very simple theme based on the archlinux-simplyblack theme provided in the archlinux-themes-slim package. I dislike all the options crap typically displayed in a login manager, so this theme will not show a user selection dialog, session manager, keyboard layout changer, language selection or even a quit dialog, no matter what your configuration is. Also my guess is that this theme only works with the GTK greeter given I have not tested anything else… Welcome back to the ongoing series of posts about my adventures in playing old games from my childhood. I know that in
Welcome back to the ongoing series of posts about my adventures in playing old games from my childhood. I know that in  Onto the actual game. Our hero is famous archaeologist and part time treasure hunter Alabama “Al” Smith, a character not too subtly modelled after Indiana Jones. Unfortunately of late his fame has been slipping with people like Bart Simpson and Oprah Winfrey taking his spotlight. So Al studies his ancient texts and finds reference to an ancient pyramid called Paganitzu, meaning “Temple of the Gods”. Rumoured to be inside this pyramid are objects of great power including the Crystal Rose, a jeweled flower that will bring peace to the man who holds it, and the Silver Dagger, which gives the strength of the gods to it wielder. So off to remote southern Mexico where Al finds a grassy hill in an otherwise flat area. Sure enough, this is the temple he is looking for and there is the entrance…
Onto the actual game. Our hero is famous archaeologist and part time treasure hunter Alabama “Al” Smith, a character not too subtly modelled after Indiana Jones. Unfortunately of late his fame has been slipping with people like Bart Simpson and Oprah Winfrey taking his spotlight. So Al studies his ancient texts and finds reference to an ancient pyramid called Paganitzu, meaning “Temple of the Gods”. Rumoured to be inside this pyramid are objects of great power including the Crystal Rose, a jeweled flower that will bring peace to the man who holds it, and the Silver Dagger, which gives the strength of the gods to it wielder. So off to remote southern Mexico where Al finds a grassy hill in an otherwise flat area. Sure enough, this is the temple he is looking for and there is the entrance… Releasing evil gods is usually not a good thing and Omigosh is no exception. He travels deeper into the pyramid and plans to raise an army of undead to destroy the world. Understandably, Al feels a bit guilty about causing impending destruction and decides to go find the Silver Dagger in the aptly named “Part 2: Quest for the Silver Dagger”. While the overall style of the game remains the same, as we delve deeper into the pyramid it has now become hot and lava filled. Along with a selection of new monsters, this gives quite a different feel to part two of the game. The strategies required for solving the puzzles also shift to quite an extent with this change to make the puzzle solving a challenge again.
Releasing evil gods is usually not a good thing and Omigosh is no exception. He travels deeper into the pyramid and plans to raise an army of undead to destroy the world. Understandably, Al feels a bit guilty about causing impending destruction and decides to go find the Silver Dagger in the aptly named “Part 2: Quest for the Silver Dagger”. While the overall style of the game remains the same, as we delve deeper into the pyramid it has now become hot and lava filled. Along with a selection of new monsters, this gives quite a different feel to part two of the game. The strategies required for solving the puzzles also shift to quite an extent with this change to make the puzzle solving a challenge again. Little things like being a ghost are not going to stop our hero. In fact, now he is already dead, travelling back in time does not seem such a bad idea… So onward to “Part 3: Jewel of the Yucatan”. The first thing Al notices is that the pyramid as seen by the dead is a living entity with walls made out of a quivering biomass. This makes for a third style to the games levels, which, along with the addition of some new deadly creatures (ghosts are not immune to being attacked) and new puzzle elements, changes the style of game play yet again. I am not sure if I was just doing the levels in novel ways, but I found there was a lot more usage of moving enemies to block other enemies and having to time movements precisely, bringing more of an action feel to the final part. Another twenty levels and we make it back to the Skull Oracle. Why were you now twenty levels away from the Skull Oracle when you only travelled ten levels away in Part 2? These are the mysteries of the pyramid that are not meant to be solved by the likes of us…
Little things like being a ghost are not going to stop our hero. In fact, now he is already dead, travelling back in time does not seem such a bad idea… So onward to “Part 3: Jewel of the Yucatan”. The first thing Al notices is that the pyramid as seen by the dead is a living entity with walls made out of a quivering biomass. This makes for a third style to the games levels, which, along with the addition of some new deadly creatures (ghosts are not immune to being attacked) and new puzzle elements, changes the style of game play yet again. I am not sure if I was just doing the levels in novel ways, but I found there was a lot more usage of moving enemies to block other enemies and having to time movements precisely, bringing more of an action feel to the final part. Another twenty levels and we make it back to the Skull Oracle. Why were you now twenty levels away from the Skull Oracle when you only travelled ten levels away in Part 2? These are the mysteries of the pyramid that are not meant to be solved by the likes of us… The final episode finishes with a stunning two hour cinematic! OK… it is apparently only 17 minutes long but it certainly takes a while to sit and watch. The Skull Oracle sends our hero back in time 500 years to get the magician Debasco to come save the world. Debasco is nice enough to restore Al back to life and so Al rewards him by getting it on with his daughter Maria, coincidentally being the woman whose body Omigosh inhabits in the future. Unfortunately, Debasco can only take one person with him to the future and that must be Al (or he could affect the space-time continuum), so his daughter gets left behind to be brutally murdered by the invading Spaniards (seriously, that is almost word for word…). Back in the future, the battle between Debasco and Omigosh looks helpless, until somehow the spirit of Maria banishes Omigosh from her body and Debasco can take him to the firely pits of hell. Al and Maria celebrate the vanquishing of Omigosh (seemingly ignoring the fact her father died…) and walk off into the sunset. You would think that 500 years of decay would be off-putting for a man, but you have to Al credit. As an archaeologist, I guess he likes old things…
The final episode finishes with a stunning two hour cinematic! OK… it is apparently only 17 minutes long but it certainly takes a while to sit and watch. The Skull Oracle sends our hero back in time 500 years to get the magician Debasco to come save the world. Debasco is nice enough to restore Al back to life and so Al rewards him by getting it on with his daughter Maria, coincidentally being the woman whose body Omigosh inhabits in the future. Unfortunately, Debasco can only take one person with him to the future and that must be Al (or he could affect the space-time continuum), so his daughter gets left behind to be brutally murdered by the invading Spaniards (seriously, that is almost word for word…). Back in the future, the battle between Debasco and Omigosh looks helpless, until somehow the spirit of Maria banishes Omigosh from her body and Debasco can take him to the firely pits of hell. Al and Maria celebrate the vanquishing of Omigosh (seemingly ignoring the fact her father died…) and walk off into the sunset. You would think that 500 years of decay would be off-putting for a man, but you have to Al credit. As an archaeologist, I guess he likes old things…